Threat Modelling
Threat modelling is defence in depth
Our threat modelling methodology evaluates your applications piece by piece to ensure security gaps are found and plugged.
What is threat modelling?
Fully understanding the security and business risks an application poses requires in-depth assessment. While many automated tools exist to try to answer this question, many fall short as they pick up low-hanging fruit only, and the nature of more subtle risks is that more context is needed. That's why we use threat modelling as our primary tool for informing our customers' risk positions.
Threat Modelling is an industry practice that has been in use for many years and is now seeing a resurgence in security circles as an increasingly effective method to identify security vulnerabilities in the age of agile software development.
You can find out more about threat modelling by downloading our brochure. Click the button below to get it; no registration required.
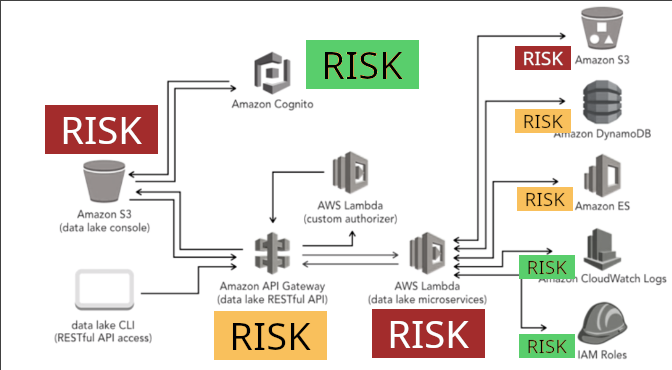
How is our approach unique?
We take threat modelling to the next level by not just assessing threats, but assessing them against the customer's risk appetite, and including extensive options for reducing or eliminating the risks posed by each threat. Feedback from previous customers proves our approach adds tremendous value to the traditional threat model and gives them the guidance needed to immediately tackle problematic threats.
Our threat models also serve as a communication tool for security teams: both to engineers who can understand what security controls apply and why, and to upper management who can interpret the summary to understand relevant business risk.
How do I get started?
Turn your security into a proactive, business-driven function, rather than a cost dictated by the attacker. Book a consultation call with us today to speak to us about threat modelling an application for you. This is a free call to discuss your needs and our service. You are under no pressure to make a purchase.

Our Threat Modelling approach is flexible by design. All of the following can be threat modelled:
- Pure Cloud Applications
- Mixed Cloud/On-prem Applications
- Applications at the concept or design stage (i.e. do not exist or are not yet in production)
- Business Processes
That's right, you can threat model applications that do not yet exist. A high-level concept or design is best to work with but minimal detail is fine. This makes threat modelling suitable for feasibility studies, architecture/design concepts and new line-of-business applications.
Business processes can also be threat modelled, in other words threat modelling doesn't just apply to purely technical processes.







